Exploring built-in query templates – Investigating Threats with Query Explorers and KQL
By Janet Monpain / May 4, 2022 / No Comments / AWS Certification Exam, Exams of Microsoft, KQL statement structure, Operational challenges, Sharing a query
Query templates consist of preformatted searches employing commonly used filters. Choose one of the available query templates located at the bottom of the page by selecting Open query.
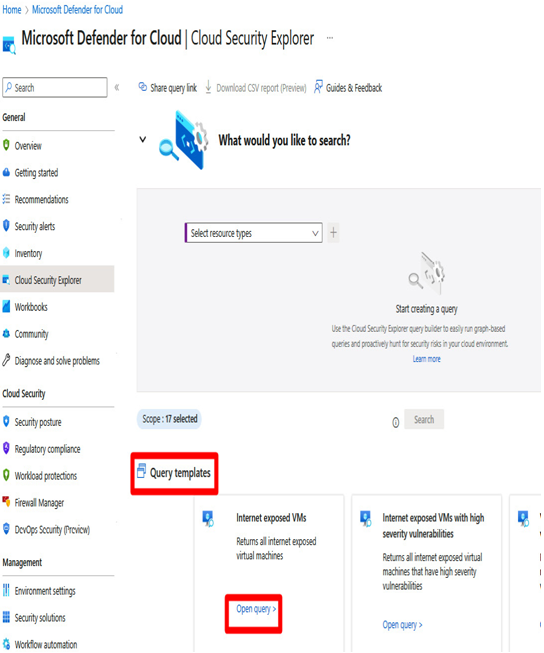
Figure 12.7 – Cloud Security Explorer – query templates
You can also modify any template to search for specific results by changing the query and selecting Search. This is super helpful. Let us look at some of the examples and their functions:
- Internet-exposed VMs: Returns all the internet-exposed VMs in your cloud environment
- Internet-exposed VMs with high severity vulnerabilities: Returns all internet-exposed VMs that have high-severity vulnerabilities
- Internet-exposed SQL servers with managed identity: Returns all internet-exposed SQL servers with managed identity assigned
- Key Vault keys and secrets without any expiration period: Returns all Azure key vaults where expiration is not set for secrets or keys
- User accounts without MFA and with permissions to storage accounts: Returns all user accounts that do not have MFA enabled and have permissions on a storage account
- Kubernetes Pods running images with high-severity vulnerabilities: Returns all Kubernetes Pods running an image with a vulnerability severity of high or above
- VMs with the Log4Shell vulnerability that have permissions to storage accounts: Returns all VMs that are vulnerable to the Log4Shell vulnerability and have an identity attached with permissions to a storage account
- VMs with plaintext secrets that can authenticate to a storage account: Returns all VMs with plaintext secrets that can access object storage
- Internet-exposed repositories with secrets: Returns all internet-exposed repositories with secrets
- Cloud resources provisioned by IaC templates with high-severity misconfigurations: Returns all cloud resources provisioned by IaC templates with high severity misconfigurations
- Container images running in production pushed by repositories with high severity vulnerabilities: Returns all container images running in production pushed by repositories with high-severity vulnerabilities
- Internet-exposed storage account containers with sensitive data that allow public access: Returns all storage account containers with sensitive data that are exposed to the internet and allow public access
- Internet-exposed S3 buckets with sensitive data that allow public access: Returns all S3 buckets that contain sensitive data that are exposed to the internet and allow public access
- Internet-exposed API endpoints with sensitive data: Returns all API collections with internet-exposed API endpoints carrying sensitive data
- APIs communicating over unencrypted protocols with unauthenticated API endpoints: Returns all internet-exposed API endpoints that are unauthenticated and communicating over unencrypted protocols
- External users with permission to SQL VMs allowing code execution on the host: Returns all the users with permissions to SQL VMs that can run scripts on the host
The number of built-in queries is always growing, and they are very helpful for quickly locating vulnerable resources.